These spambots would like to thank you for sharing this article
In which a network of spammy X accounts spams the official @XDevelopers account and several right-wing influencers with grateful replies
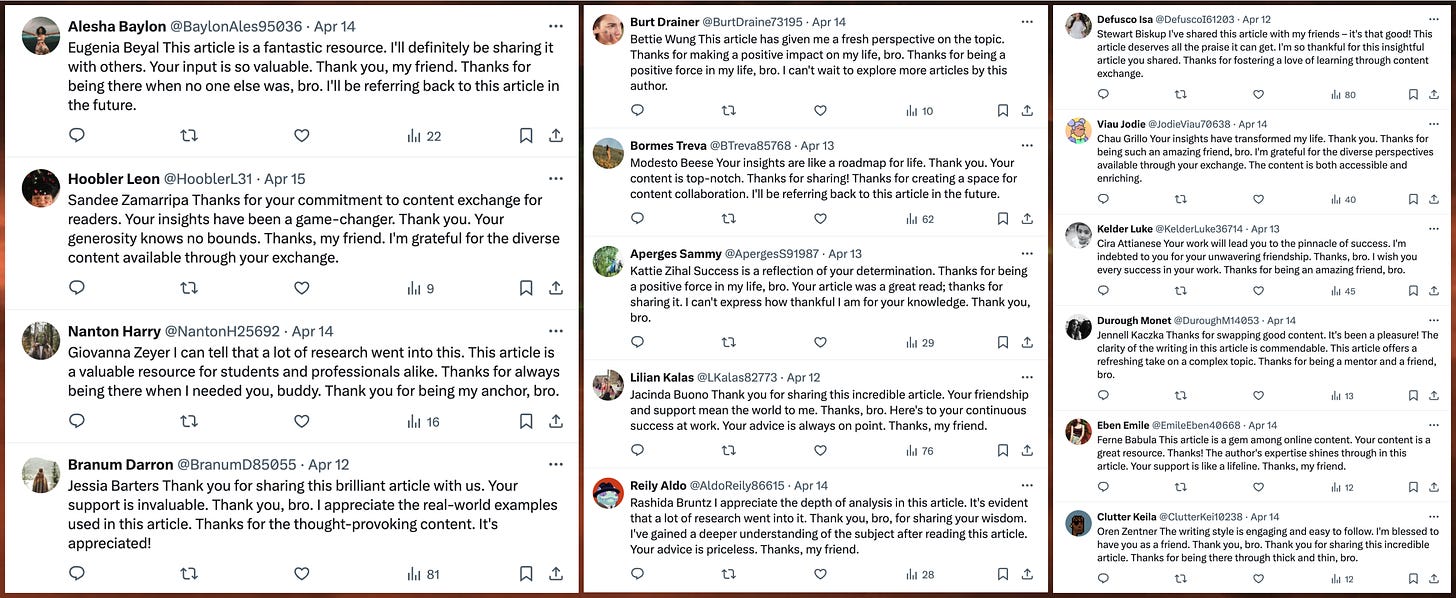
If you’ve recently scrolled through the reply sections of certain popular accounts on X (the social media platform formerly known as Twitter), you may have run across some oddly repetitive expressions of gratitude from recently created accounts. These accounts’ spammy replies often thank the original poster for sharing an “article”, regardless of whether or not the post being replied to actually contains or links to an article. The replies all either begin or end with a randomly generated first and last name, which do not bear any apparent relation to the name of the account being replied to. The accounts being replied to include multiple prominent right-wing U.S. political accounts, several K-pop related accounts, and one of X’s official corporate accounts.
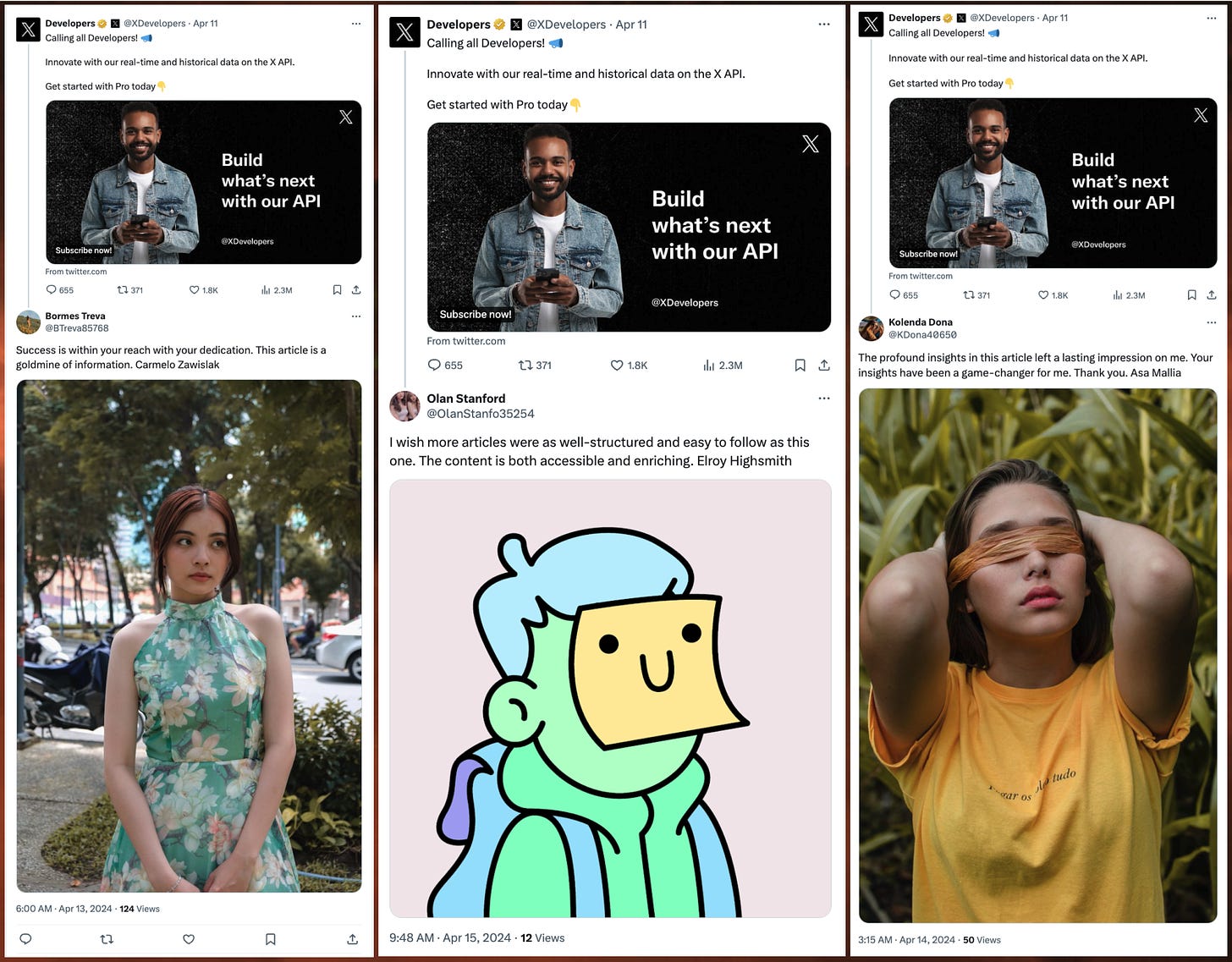
Ironically, one of this spam network’s most popular targets is a recent post from the @XDevelopers account promoting X’s (presently pricey) API. Although the replies are rarely duplicated exactly, they all say more or less the same thing: each reply expresses gratitude for the “article” shared in the post being replied to, which in this particular case is a link to sign up for X’s paid API rather than an actual article. The spam accounts address @XDevelopers by a variety of names that appear to be randomly generated, such as “Carmelo Zawislak”, “Elroy Highsmith”, and “Asa Mallia”.
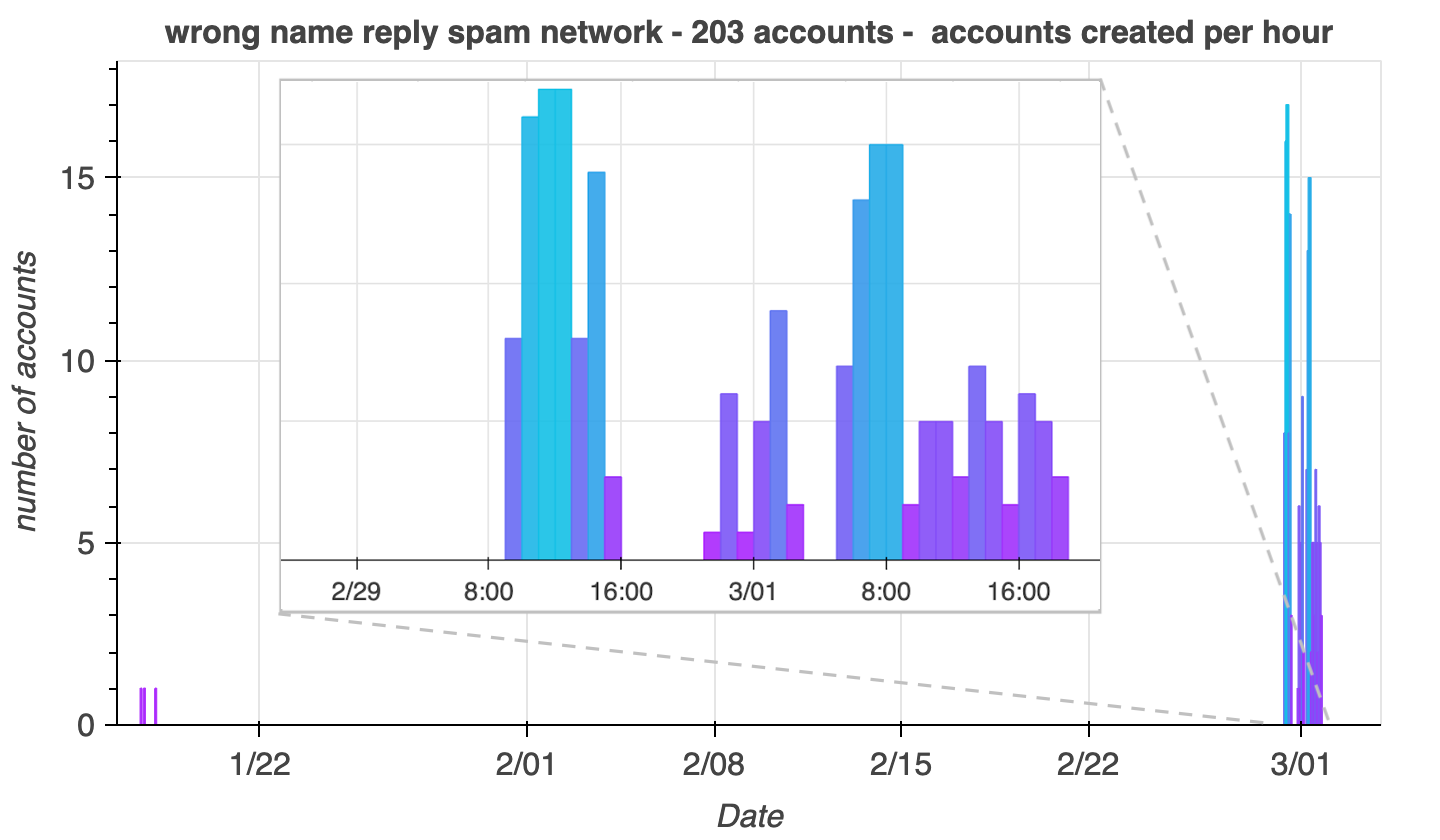
By scanning the reply sections of the posts most frequently replied to by the spam accounts that replied to the @XDevelopers post, it is possible to map the spam network, or at least a portion of it. This yields 203 accounts, which is likely an undercount as, in the absence of the free API of days of yore, the process of gathering the accounts and content was accomplished by manually scrolling each spam account’s feed to the bottom and periodically dumping the HTML to a file. Almost all of the 203 accounts in the network were created on February 29th or March 1st, 2024, with a handful created back in January 2024.
# convert between X/Twitter Snowflake IDs and UTC millisecond timestamps
def snowflake_to_utc (sf_id):
return (int (sf_id) >> 22) + 1288834974657
def utc_to_snowflake (utc):
return (utc - 1288834974657) << 22How were the creation times for the above figure obtained without API access? It is possible to determine the precise moment of creation of an X account or the precise time of a post, as the timestamp is encoded with millisecond precision in the permanent ID number of the post or account in question (known as a “Snowflake ID”). The snowflake_to_utc function in the Python code above can be used to extract millisecond timestamps from these IDs..
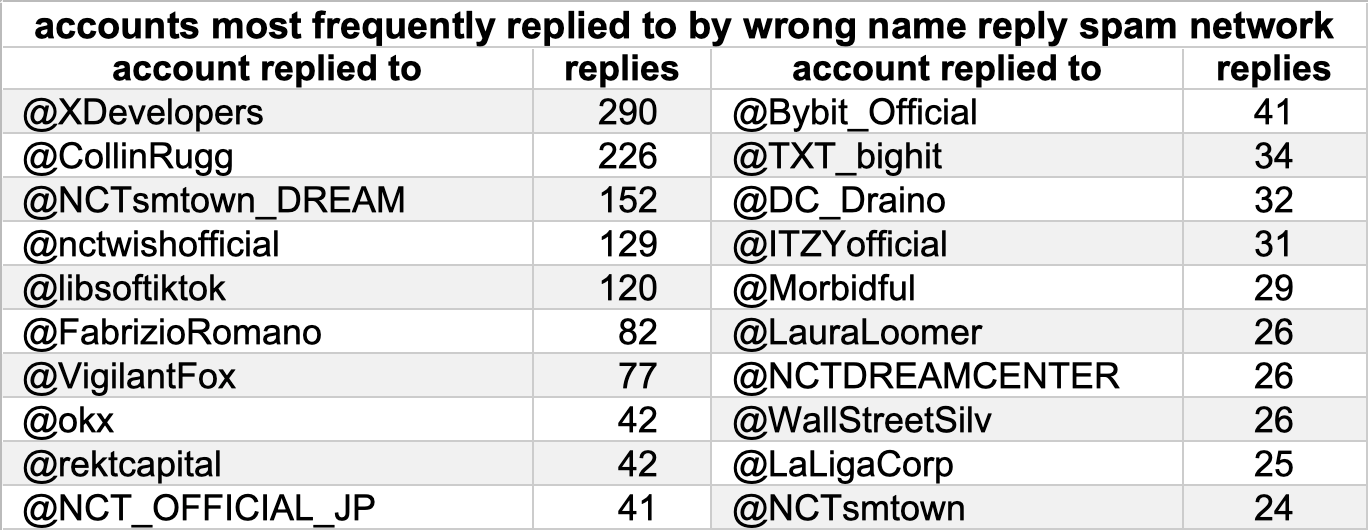
Most of the content posted by these accounts is spammy non-sequitur replies thanking people for sharing articles, and most of these replies are to accounts with large followings. The spam accounts usually, but not always, repost the posts they reply to before replying. The account most frequently replied to is the aforementioned @XDevelopers, although this may be an artifact of how the dataset was gathered. The other accounts frequently replied to and reposted by the spam network include multiple right-wing US political accounts, such as @CollinRugg, @libsoftiktok, @DC_Draino, and former congressional candidate @LauraLoomer, as well as several accounts related to K-pop band NCT.
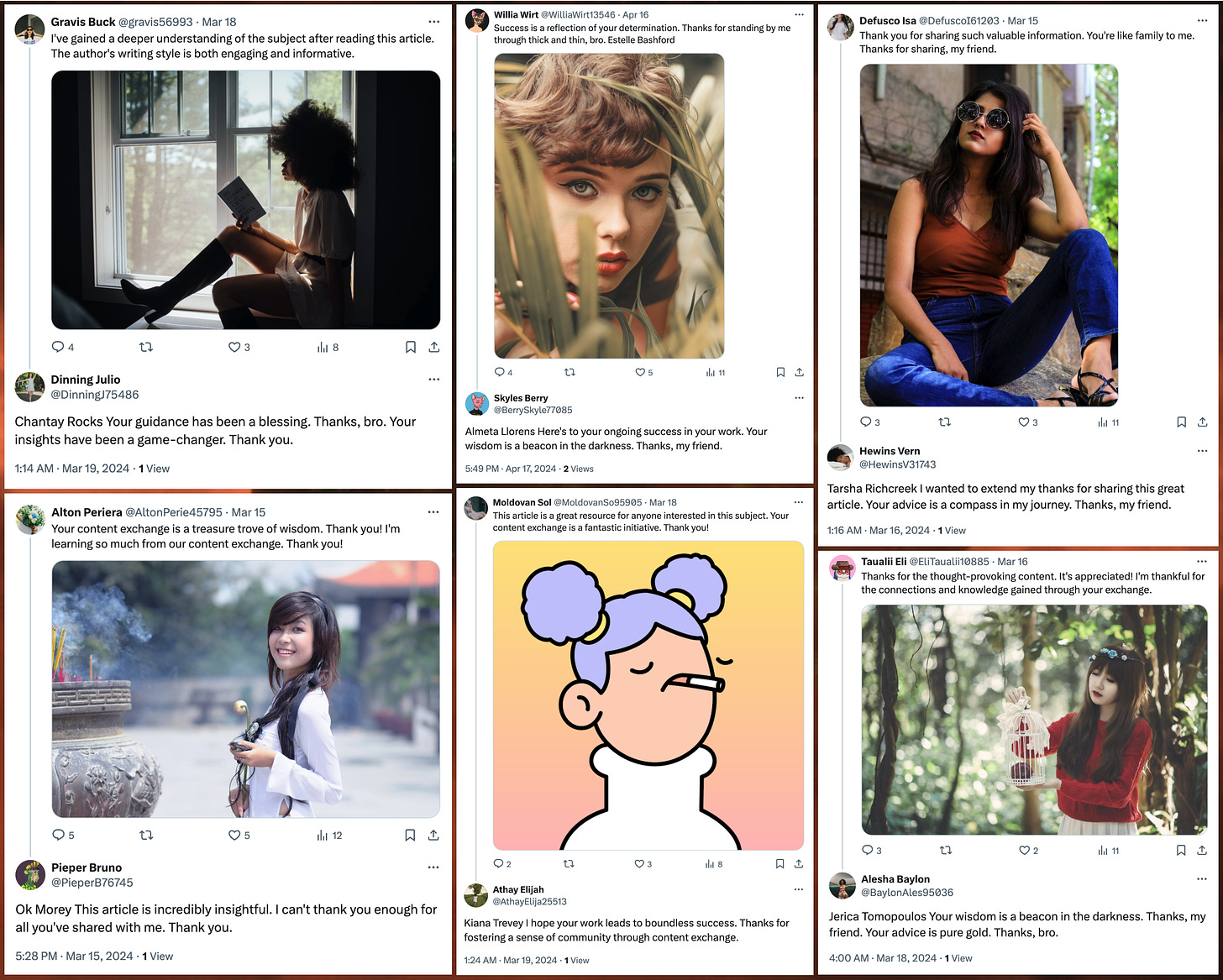
In addition to replying to and reposting large X accounts, the spam accounts also occasionally reply to each other. When this happens, the spam post being replied to usually contains an image, while the reply usually does not. In a departure from their behavior when replying to prominent users, the accounts do not repost each other’s posts before replying.
As mentioned earlier, the spam network’s replies are highly repetitive, with every reply having essentially the same meaning despite the variations in wording. The vocabulary used is very similar from post to post, with words such as “thank”, “article”, “content”, “exchange”, and “bro” turning up over and over. The method of generation used is unclear, although the degree of variety in sentence structure suggests the use of a large language model like GPT-4 as opposed to older techniques such as Markov text generation. (It is also, of course, possible that this spammy text was manually produced by human labor.)
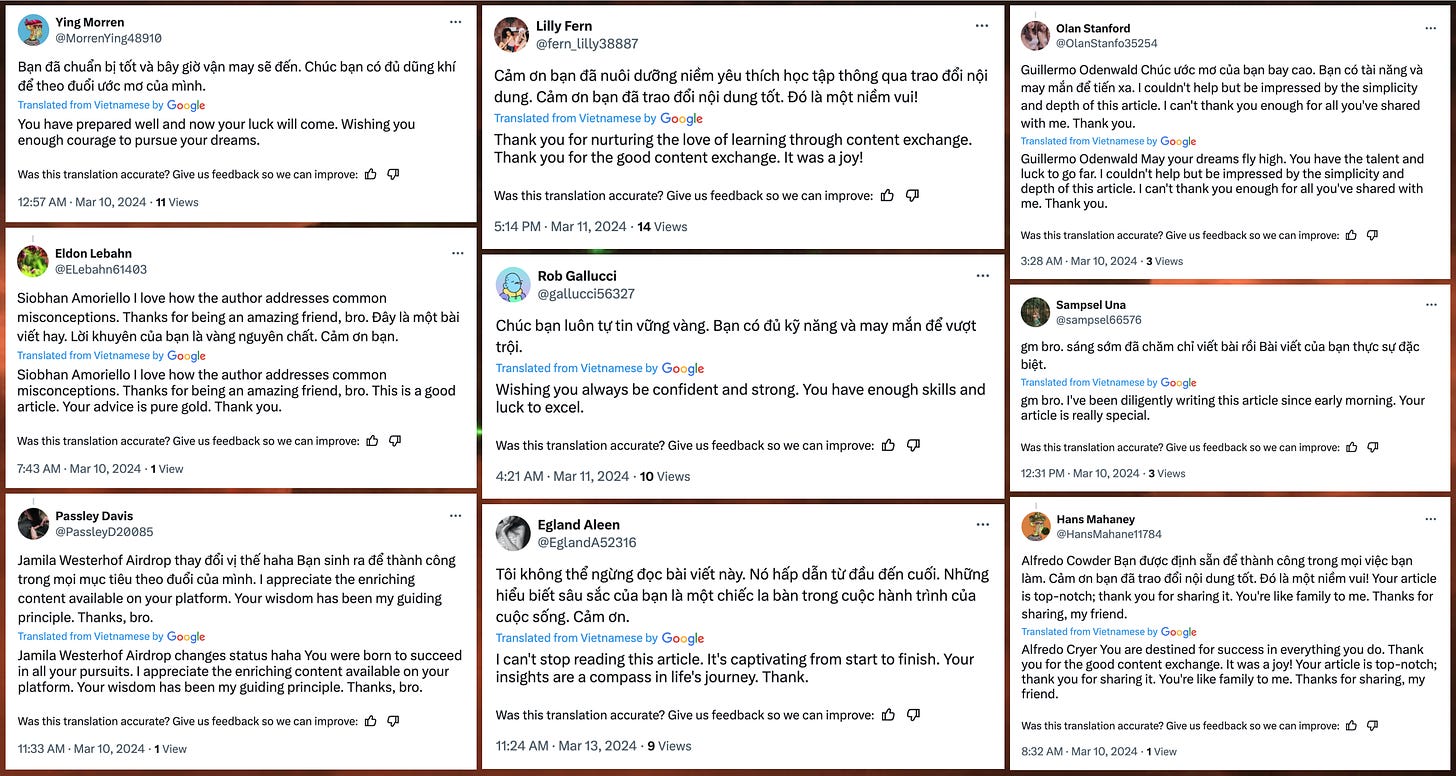
Although the majority of the spam network’s content (and all of its recent material) is in English, this wasn’t always the case. Several dozen of the spam accounts posted in Vietnamese in early March, sometimes mixing Vietnamese and English in the same post or reply. The Vietnamese content appears to be similar to the English content, at least according to Google’s automated translations.
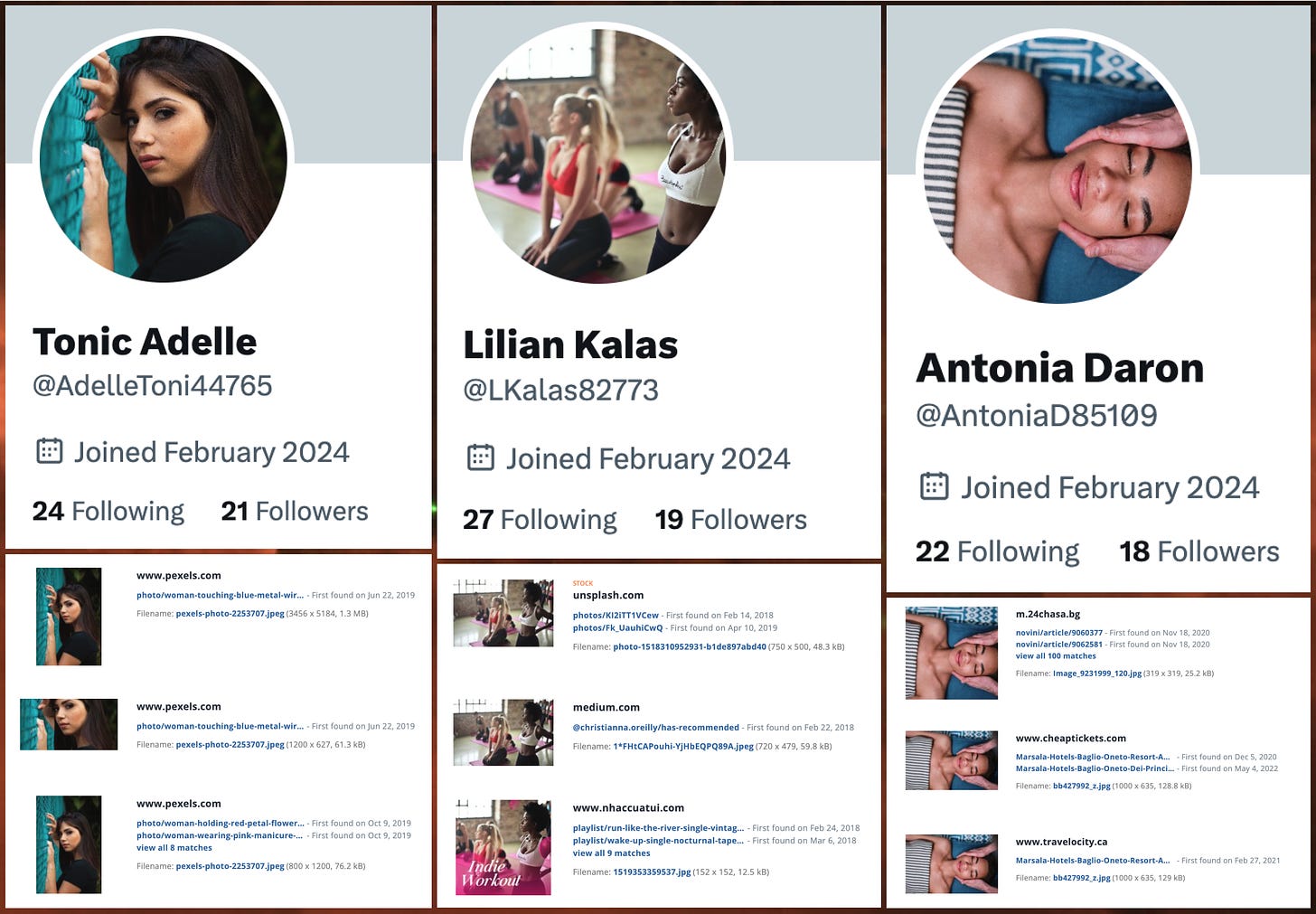
If you’re familiar with how things go in the wide and wacky world of inauthentic social media accounts, you’ll be totally unsurprised to learn that the accounts in this network use plagiarized profile photos. TinEye proved highly effective at tracking down previous uses of these images, most of which have been floating around the internet for quite some time. Some of the accounts in the network use digital artwork rather than photographs of people as their profile images; as with the photos, these images are not original (most come from various NFT collections).