Federation and political spam
Three protocols, one botnet: in which a flock of spam accounts pushed repetitive pro-Trump posts from Nostr to Bluesky via Mastodon
On May 11th, 2024, a flurry of repetitive posts with the text “remember to always vote trump” began to appear on social media platform Bluesky. This flood of low-effort political spam was posted by accounts with default avatars, and display names consisting of a random adjective and noun separated by a hyphen. The accounts and their accompanying posts were not originally created on Bluesky; instead, they were created via decentralized social networking protocol Nostr. Bluesky shut down this flow of spam within a few hours, but since these posts originated outside of Bluesky, it is still possible to do a post mortem analysis of this cross platform pro-Trump spam network.
What is Nostr, and how is it related to Bluesky? Nostr is an open protocol for decentralized social media services, and has some similarities to Bluesky’s AT Protocol and Mastodon’s ActivityPub, albeit a bit more bare-bones and with some interesting differences. For example, Nostr technically has no user accounts; each “user” is simply a public/private key pair, where the user’s public key serves as their publicly visible unique ID. The server-side functionality of Nostr is provided by a system of relays, which can be federated so that posts (known as “events”) created on one relay may propagate to other relays.
How did the pro-Trump spam posts make their way from Nostr to Bluesky? First, the Nostr content was propagated to Mastodon (based on the ActivityPub protocol) via Momostr.pink. Then, a tool called Bridgy Fed was used to push the content from Mastodon onto Bluesky. Fingerprints of this process appear in the Bluesky versions of the posts, where the account handles have the format npub************.momostr.pink.ap.brid.gy. The first portion of this (from npub until the first dot) is the public key of the Nostr account, while the remainder (momostr.pink.ap.brid.gy) contains some indications as to the tools used to bridge the posts (Momostr and Bridgy Fed).
from datetime import timedelta
import json
from nostr_sdk import Client, Filter, PublicKey
import pandas as pd
df = pd.read_csv ("remember_trump_bsky_profiles.csv")
df["npub"] = df["handle"].apply (lambda h: h[:h.find (".")])
df["bridge"] = df["handle"].apply (lambda h: h[h.find (".") + 1:])
df = df[df["bridge"].str.contains ("brid.gy")]
keys = [PublicKey.parse (npub) for npub in df["npub"]]
df["pubkey"] = [key.to_hex () for key in keys]
client = Client (None)
client.add_relays ([
"wss://relay.nostr.band"
])
client.connect ()
events = client.get_events_of ([Filter ().authors (keys)],
timedelta (seconds=8640000))
df_events = pd.DataFrame ([
json.loads (event.as_json ()) for event in events])
df = df.merge (df_events, on="pubkey")
df.to_csv ("remember_trump_nostr_events.csv", index=False)As mentioned earlier, Bluesky has already taken action against this set of spam accounts. Moderation actions taken by Bluesky do not propagate back to the original Nostr posts, however, which means those posts are still available for analysis. The above Python code makes use of the nostr_sdk library to retrieve the content posted by a set of 228 accounts whose handles were captured during the May 11th spam campaign. (This dataset is likely incomplete, as Bluesky started removing the accounts while the data was being gathered, hence the need to harvest the content from Nostr instead.)
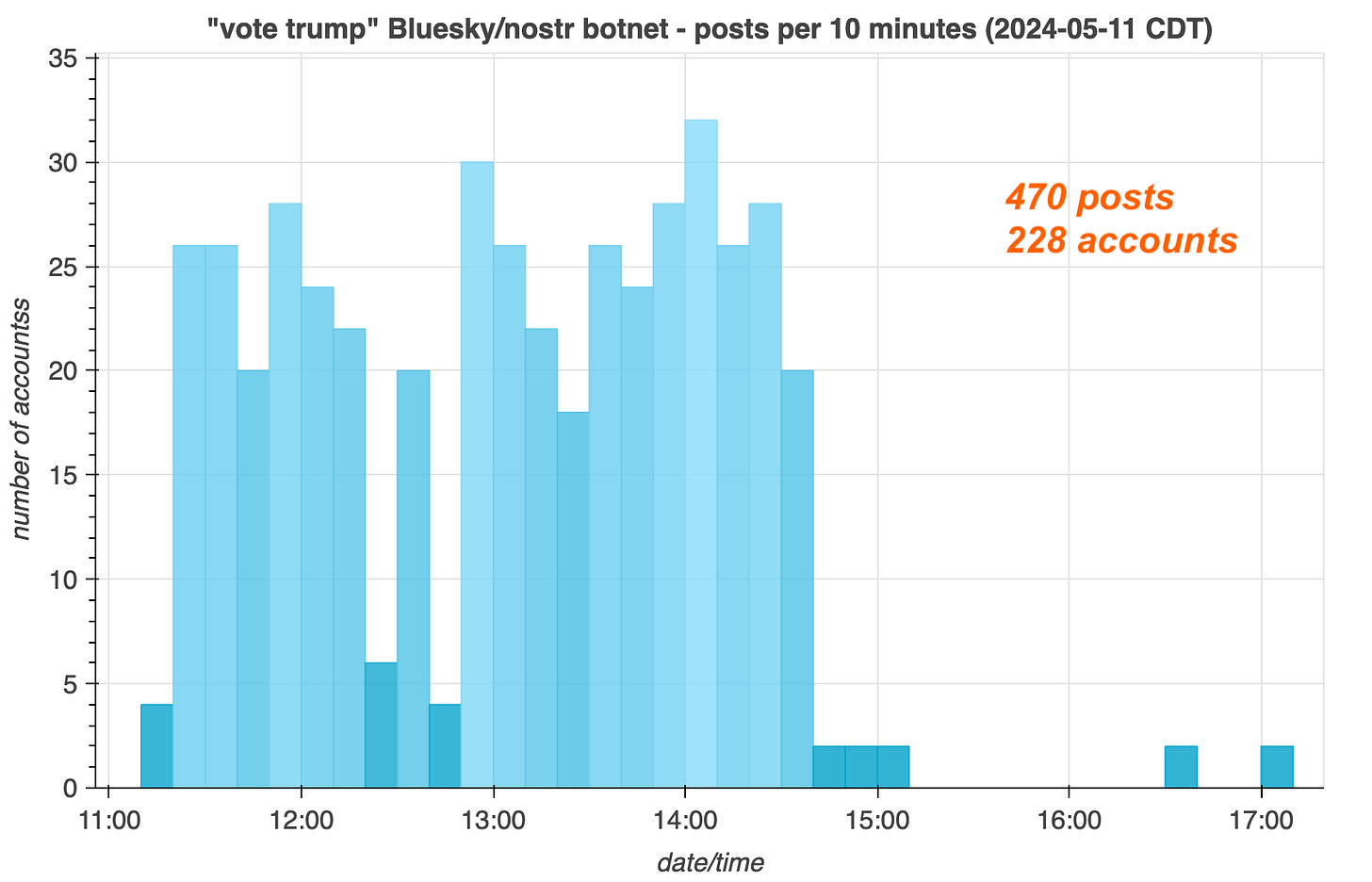
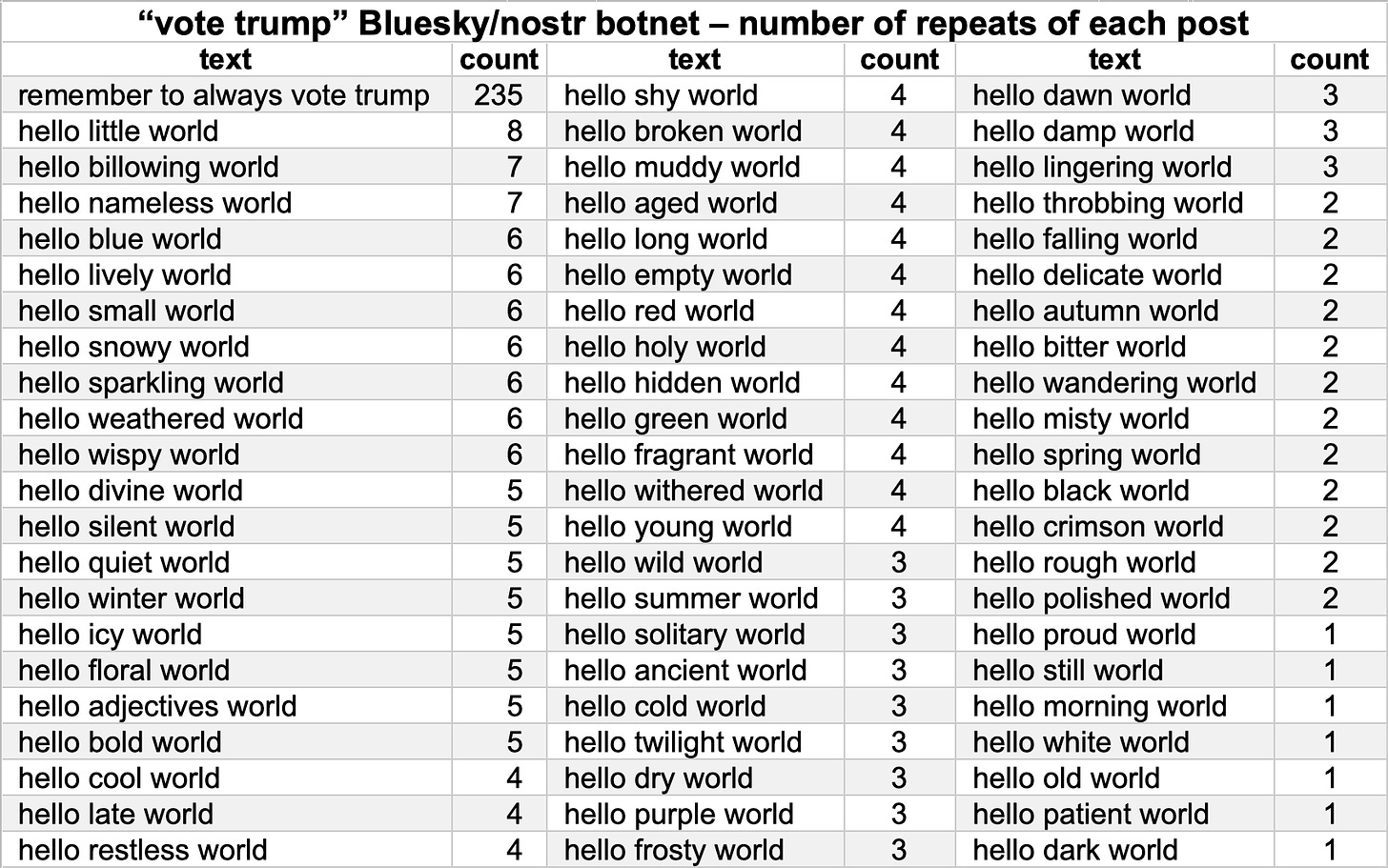
These 228 accounts posted a total of 470 times over the course of roughly six hours on May 11th, 2024. Each account in the network posted the text “remember to always vote trump” either once or twice, comprising exactly half of the network’s content (235 of 470 posts). The remaining posts are all of the form “hello <X> world”, where X is a random adjective (or, in one case, the word “adjectives”). The network has posted 65 distinct variations of the “hello world” posts, with the most frequent being “hello little world”, “hello billowing world”, and “hello nameless world”, and each account has the same number of “hello world” posts as “remember to always vote trump” posts.
Correction 2024-05-21: The original version of this article incorrectly stated that the Mostr Bridge (mostr.pub) was used to bridge posts from Nostr to Mastodon. This has been updated to correctly reflect that Momostr.pink was used for this purpose.

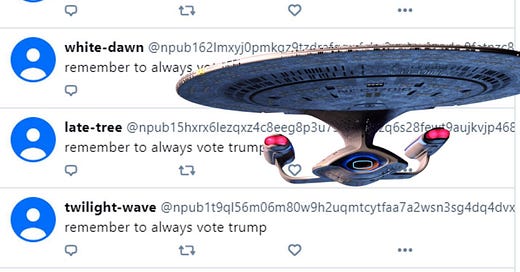


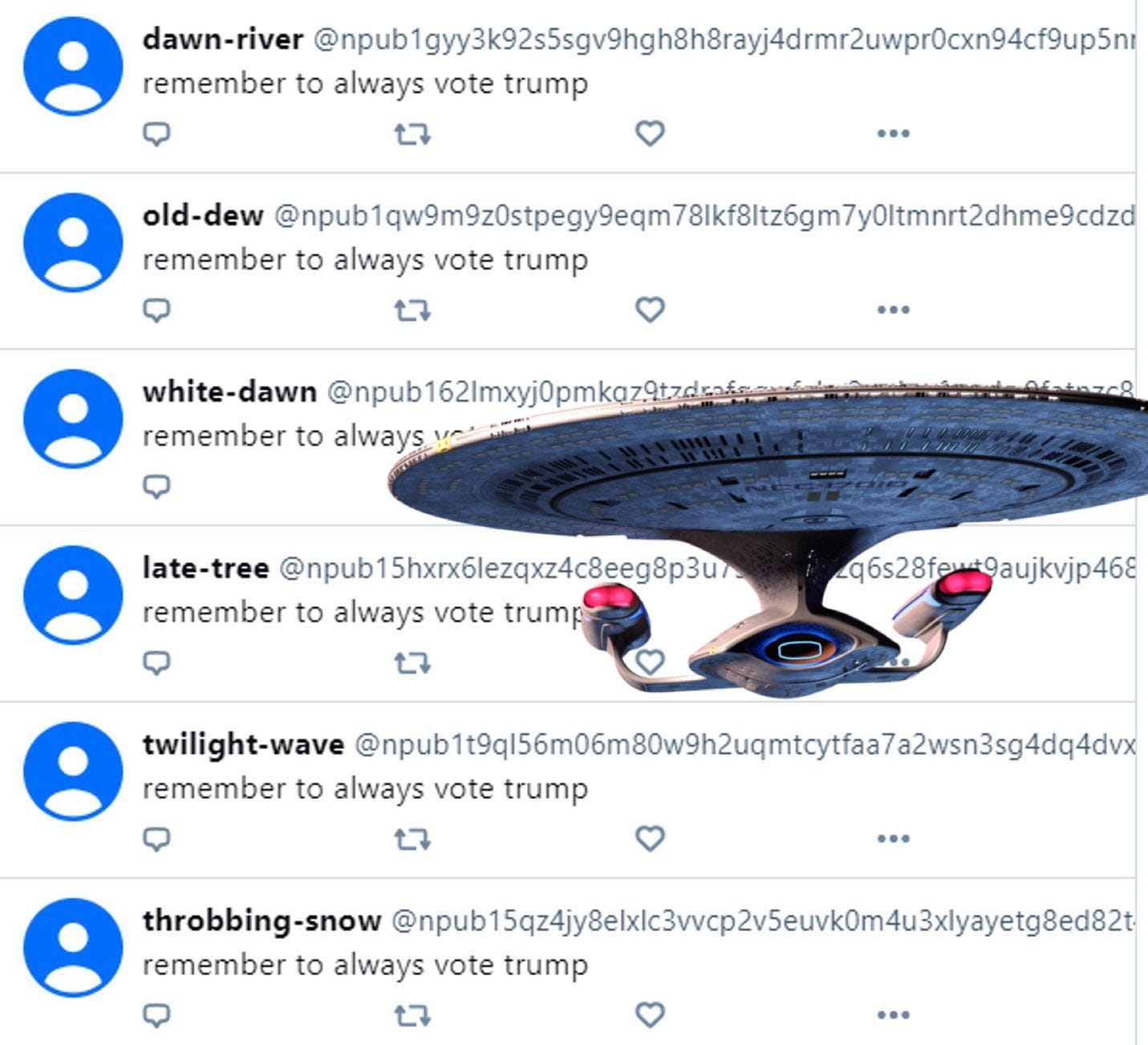
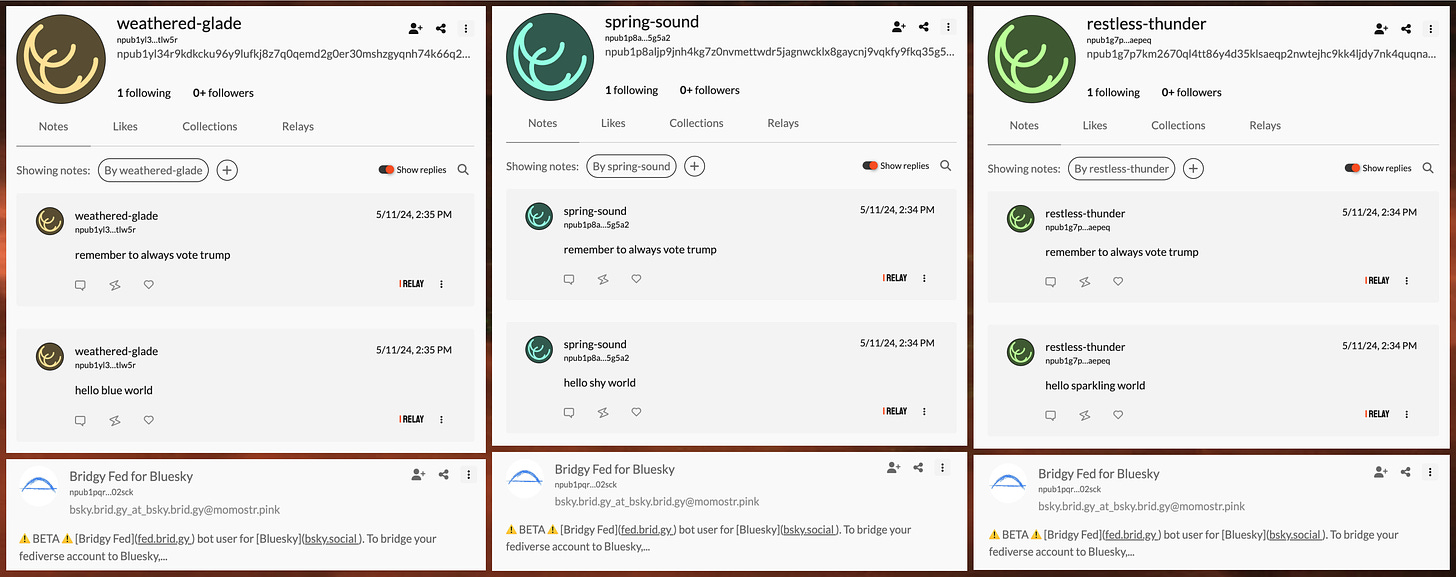
Hello, you are spreading misinformation about the Mostr Bridge, which has a built in antispam system. If you look at your own screenshots you'll see the spam is from momostr.pink, NOT mostr.pub. Momostr is a separate service developed independently by a separate person and has nothing to do with the blog post you linked at Soapbox! Please remove that and clarify.